Since the dedaub smart contract monitoring service has been active for over a year, it’s now time for members to review and evaluate whether or not the mutual should continue to provide funding for this service.
In this post, I’ll review the cost of the dedaub smart contract monitoring service to date, the projected costs, and the impact on Nexus Treasury holdings.
Overview
In May 2021, members voted to work with dedaub to monitor select smart contract systems for vulnerabilities to mitigate potential claimable events. After this vote passed, the Nexus Mutual team worked with dedaub to create, install, and maintain a vulnerability analysis and continuous monitoring service over select smart contract systems that the mutual covers.
Question for members
These monthly payments are made in wNXM, and since wNXM trades below book value, these monthly payments have a larger impact on DAO treasury funding. The bear market has impacted the value of funds held in the DAO treasury since the proposal was first passed.
The continued monthly cost for this program represents 0.65% of the current value of the treasury and the annualized cost is 7.76% of treasury funding.
Members should discuss and decide if we should continue funding this smart contract monitoring service or if we should discontinue funding for this service.
Cost to date
As outlined in the original proposal, dedaub’s fee is $20k per month, which is paid in wNXM.
To date, the mutual has paid 10,102.79 wNXM for dedaub’s smart contract monitoring service.
Projected cost
To continue this service, the cost will remain $20k per month. At today’s wNXM price ($16.77), this is equal to 1,192.60 wNXM per month for the mutual to continue to monitor these smart contracts (~0.65% of current treasury funding).
The annual cost would be $240k per year, or 14,311.27 wNXM (~7.76% of current treasury funding).
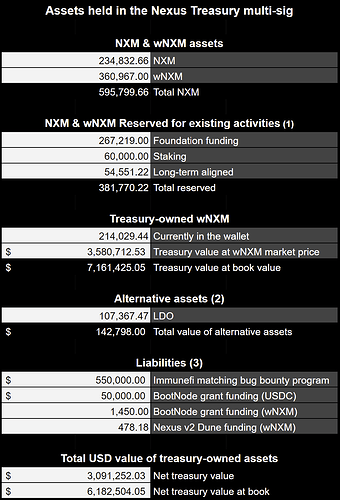
Nexus Treasury holdings
- Members voted to allocate wNXM acquired through buyback in Dec 2021 and January 2022 in the following Snapshot vote.
- LDO assets will be used to conduct a wNXM buyback according to the outcome of the following Snapshot vote.
- Funding that is currently earmarked for programs, grants.
Current smart contracts monitored by dedaub
At present, dedaub monitors the following smart contracts for the mutual:
- Nexus Mutual
- Aave v2
- AlphaHomora V2
- Argent
- BadgerDAO
- Bancor
- Compound v2
- Convex
- Curve
- Hegic
- Liquity
- mStable
- Set Protocol
- Sushiswap
- Synthetix
- Vesper
- Yearn
Past proposal, vote
- Dedaub ↔ Nexus Mutual Collaboration Proposal
- Snapshot: Should we grant Dedaub ↔ Nexus Mutual Collaboration?
Review and discussion period
This proposal will be open for discussion and review for the next ten (10) days. Members can share their thoughts, analysis, and comments below.
Once the community has weighed in and there’s a general consensus, this discussion will be transitioned to a Snapshot vote to determine whether or not this smart contract monitoring service will be continued.